6 Advanced Security Topics¶
Triofox design is a traditional 3-tier software architecture design.
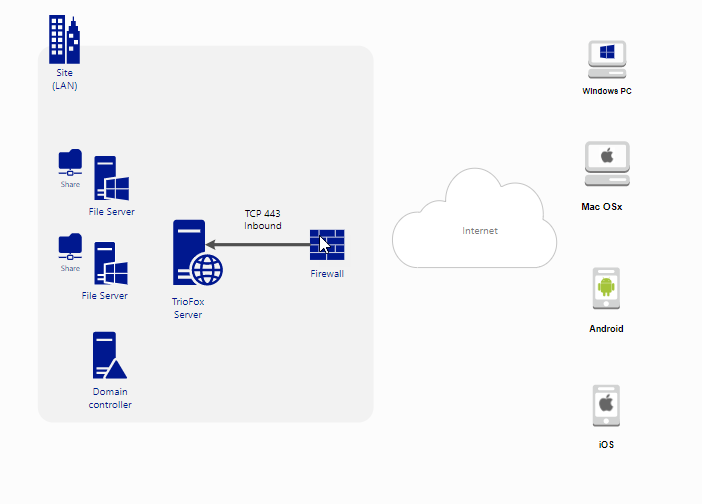
Triofox design is a traditional 3-tier software architecture design.
1. From the right, the first tier is the client access tier. This tier contains a broad list of devices such as Windows PC, Windows Server, Mac OSX, Android, iOS, Web Browser based devices and others. These devices are connected to the Internet, and with Triofox client software running. End users are using devices in this tier to access content and do file sharing and collaboration with their co-workers.
2. The second tier is the application tier; the transaction broker and the gateway between the remote client tier from the right of the diagram, to the internal IT infrastructure on the left side of the diagram, and vice versa. It is at the center of the software stack. This tier is built on top of Microsoft Web Platform, such as Internet Information Server (IIS), .NET Framework and ASP.NET. Enterprise IT will install this middle tier mostly on-premise, together or close to their own IT Infrastructure.
The third tier is the internal infrastructure. This is where the data service (such as traditional file servers) and identity services (such as Active Directory) reside.
Application Tier¶
Triofox is a pure Windows Server software that can be installed and hosted by the enterprise IT departments. Since it is self-hosted, the data storage and data passage are under full control and enterprise IT can apply the traditional security measures to allow access to company data to their users over the internet without a VPN.
Load Balancer – A single Triofox server can support up to 10,000 users. For redundancy or for supporting larger customer base, multiple Triofox servers are required to form a Triofox server cluster. In this case, a Load Balancer is required to load balance to each individual Triofox server.
Triofox Server Worker Node – a bunch of Triofox servers. In small deployments, most of the time, one single server is enough. These servers are Windows Servers (such as Windows Server 2016 or Windows Server 2019) with IIS, .NET Framework and ASP.NET configuration and Triofox software running.
Database - The Triofox servers are connected to a single cluster by connecting to a single database. Logically the Triofox database belongs to the application tier but can also be put into the Internal Infrastructure tier.
Application Tier Security¶
Encryption
To protect customer data in transit Triofox server supports SSL 3.0/TLS 1.0 with up to 256-bit AES encryption and no less than 128-bit encryption. It leverages the Windows Server’s SSL/HTTPS support for the data-in-transit encryption. The Windows Server can be tuned into FIPS compliant mode if needed.
Data-at-Rest encryption can also be turned on. Once turned on, the client device when transferring files from the client device, will encrypt the files data-at-rest first, and after that, the files will be transferred in data-in-transit mode to where the internal infrastructure is.
Client Tier Security¶
Devices in the client tier are most exposed to security threat. There are many best practices secure software design applied to the client tier security to guard against exposure.
No Password – The most secure way to secure password is no password. Client side software applies several best cyber software practice such as never save user password to the client side. In this design, client credential and login will in return get a token, which will then be used in turn for access.
Encryption – The same encryption principle that applies to the application tier, also applies to the client tier. HTTPS/SSL is used for communication between the client tier and the application tier.
Internal Infrastructure Tier¶
This is the traditional internal infrastructure and is the most secure part as shown in the architecture diagram. Triofox allows the software to be self-installed and self-hosted in the DMZ to communicate to the internal infrastructure. This allows the IT team to secure both the internal infrastructure and the Triofox server by managing the firewall rules on both sides of the firewall.
Security Best Practices¶
Client Access Policy
Define customized access policies to restrict and allow access based on the device location. For example, a company can enable access from the internet to only Windows clients and web clients. IT can configure allow or deny client access policies from the following locations:
Access from the internet
Access from local network
Access from Anywhere
Access from customer-defined networks
Deny access from customer defined networks
The above allow and deny client access policies can be configured for the following clients:
Web client
Web management
Windows client
Mac client
Mobile client
Share Acces Policy
IT can also prevent data loss and data leakage of important company confidential shares by configuring ‘Share Access Policies’ for external users who are not company employees. You can configure allow or deny shares access policies from the following locations:
Access from the internet
Access from local network
Access from Anywhere
Access from customer-defined networks
Deny access from customer defined networks
The above allow and deny share access policies can be configured with the following conditions:
Visible
Permissions to list files
Permissions to read files
Permissions to create or update files and folders
Permissions to delete files and folders
Secure data room
Enable SSL between the client and worker nodes
You will enable SSL between the clients and the worker nodes so the communication between the access clients out there in the Internet and the worker nodes are encrypted (Data-In-Transit). The communication between the clients and the server is secured by the SSL (HTTPS).
Front Firewall HTTPS Only
For the Internet facing Firewall, you will enable the port 443 for HTTPS only.
Have an Internal Management Node
You will have most of the worker nodes under the load balancer, and servicing external requests. You can save one worker node and make it internal only. You will enable management functionalities on this management node only.
Put Backend Servers behind Second Firewall
For the storage services, the Active Directory (optional) and Database (SQL) Server, you can put it behind the second firewall.
Enable Data-At-Rest Encryption
You can turn on Data-At-Rest Encryption. The Data-At-Rest encryption is using AES 256 algorithm.
Route Traffic through Worker Nodes
If you have backend object storage services, most of the object-based storage service is directly addressable. If you want to reduce the attack surface, you can force the traffic to be routed through the worker nodes.